GNS3 Lab: GRE, IPsec, DMVPN Labs.
GRE Lab
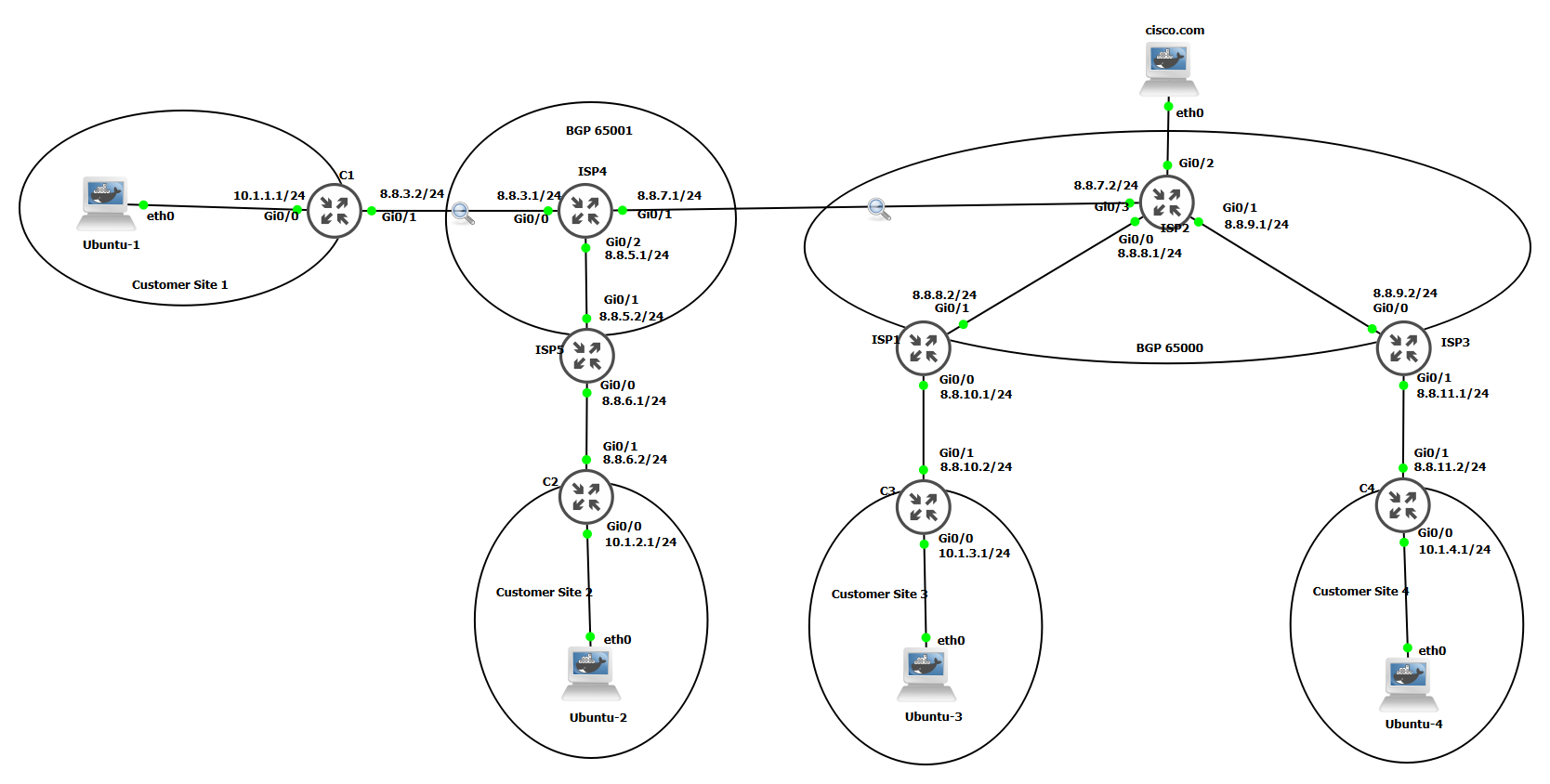
Generic Routing Encapsulation (GRE) is a tunneling protocol for encapsulating a wide variety of protocols like EIGRP, and OSPF packet types inside IP tunnels thereby generating a virtual point-to-point connection in my case C1 (10.1.3.1) to C2 (10.1.3.2) connection to routers across an IP network at remote points tunneling using GRE permits network expansion across a single-protocol backbone environment by linking multiprotocol subnetworks in a single-protocol backbone environment. The disadvantage of using this alone is it is unsecured since information is not encrypted while moving from one point to another through the internet.
For this lab, I was able to set up a GRE tunnel between C1 and C2 the ISPs represent the internet when the GRE tunnel is established Ubuntu-1 PC is able to ping Ubuntu-2 PC.
IPsec VPN
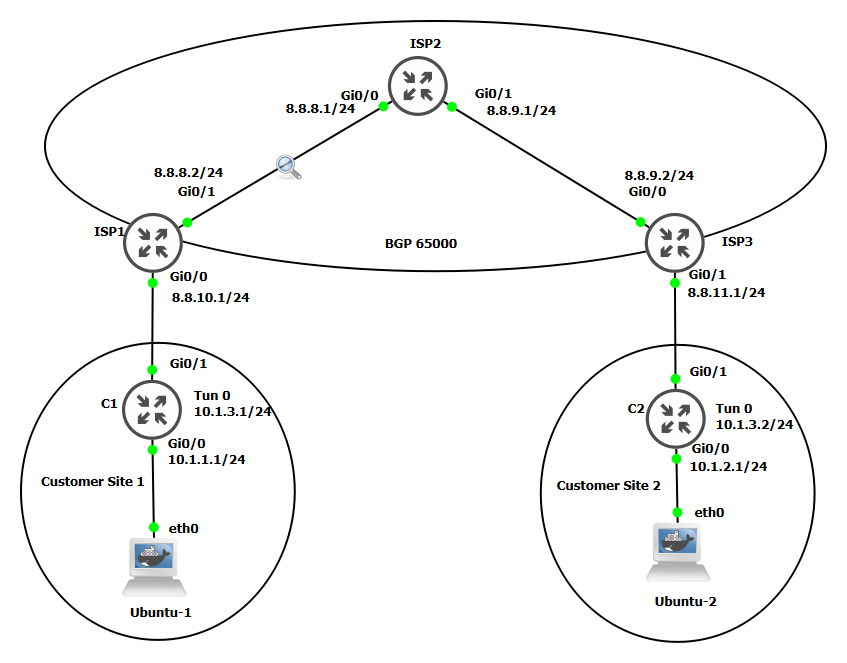
IPsec is an industry-wide standard suite of protocols and algorithms that allows for secure data transmission over an IP-based network that functions at layer 3 network of the OSI model.
Once the IPsec is set on this lab when I ping Ubuntu-1 to Ubuntu-2 and examined the packets using Wireshark. I could see ESP (Encapsulating Security Payload) meaning the information is encrypted, unlike the one for GRE.
DMVPN (Dynamic Multipoint VPN)
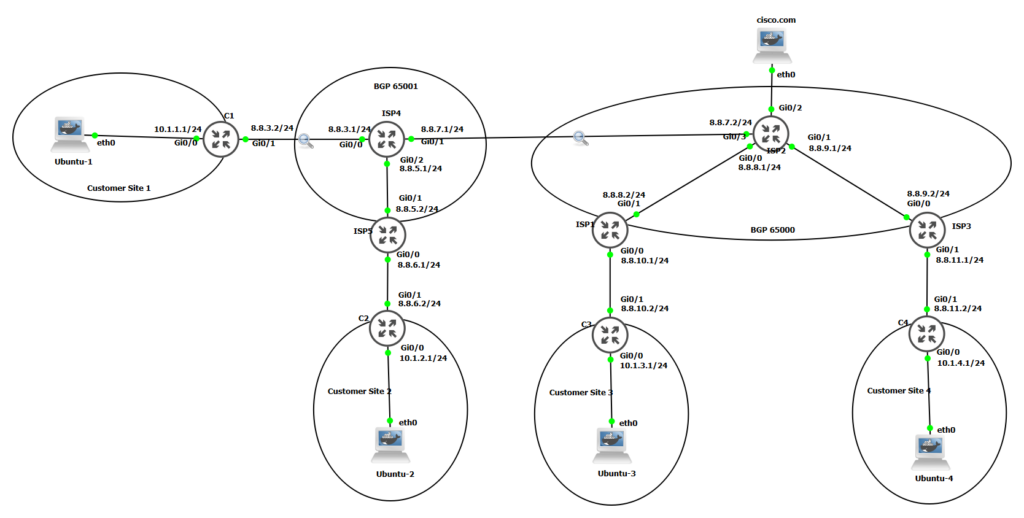
DMVPN (Dynamic Multipoint VPN) is a routing technique we can use to build a VPN network with multiple sites without having to statically configure all devices. It’s a “hub and spoke” network where the spokes will be able to communicate with each other directly without having to go through the hub. Encryption is supported through IPsec which makes DMVPN a popular choice for connecting different sites using regular Internet connections.
For the lab above CS1 is the Hub while CS2, CS3, and CS4 are the Spoke. The Dynamic Multipoint VPN (DMVPN) feature combines GRE tunnels, IPsec encryption, and NHRP(Next Hop Resolution Protocol) routing to provide ease of configuration via crypto profiles; which override the requirement for defining static crypto maps–and dynamic discovery of tunnel endpoints.
NHRP is a client-and-server protocol where the hub is the server and the spokes are the clients. The CS1(HUB) maintains an NHRP database of the public interface addresses of each CS2, CS3, and CS4 (Spoke). Each spoke registers its real address when it boots and queries the NHRP database for real addresses of the destination spokes to build direct tunnels.
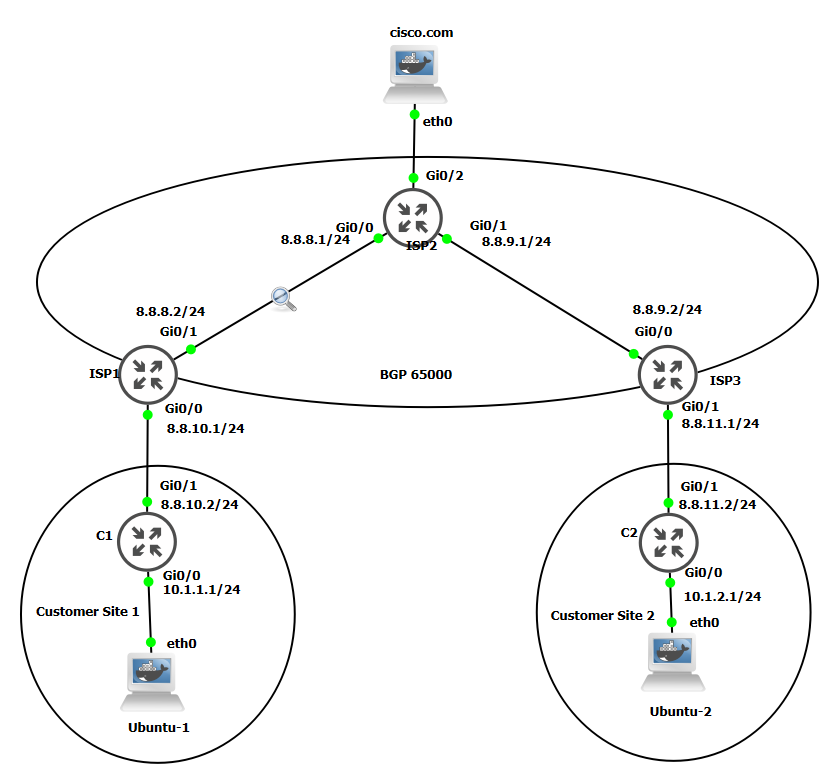
Dynamic IPsec Peers
IPsec tunnels can also be established using dynamic peer security gateways, in which the remote ends of tunnels do not have a statically assigned IP address.
Since I am not using a static IP address for CS1 and CS2. A domain name is used since the IP address of CS1 and CS2 can change.
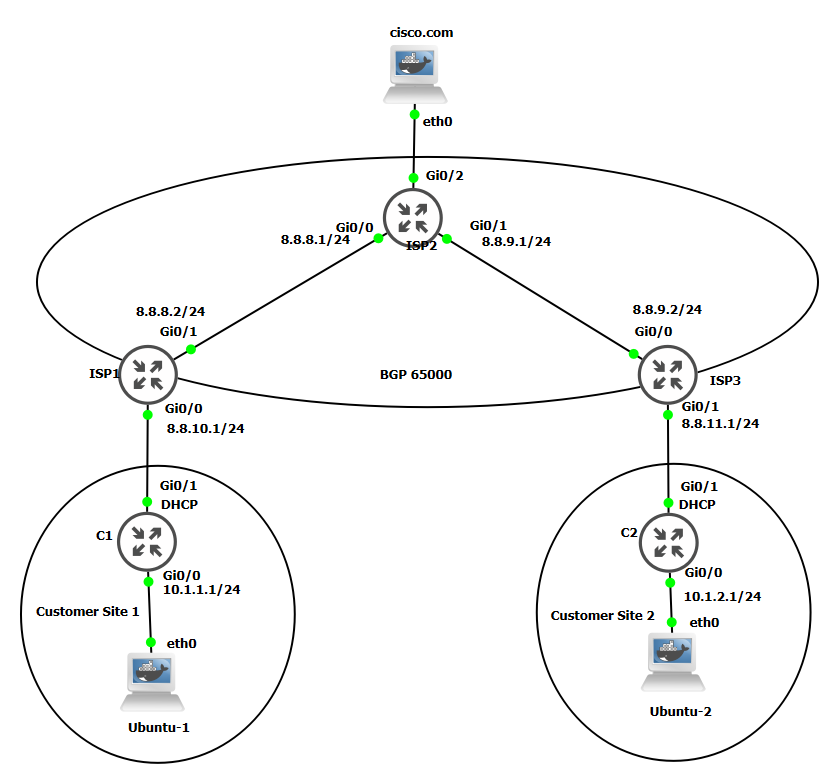
This is a summary of my documentation of the course.
Course at Udemy by David Bombal
