An access control list (ACL) is made up of rules that either allow access to a computer environment or deny it.
An access control list on a router consists of a table that stipulates which kinds of traffic are allowed to access the system. The router is placed between the incoming traffic and the rest of the network or a specific segment of the network, such as the demilitarized zone (DMZ). The ACL examines the information held within data packets flowing into or out of the network to determine where it came from and where it is going. The ACL on the router then decides whether the data packet should be allowed to pass to the other side. There are two types of ACLs used in the lab:
A standard ACL allows or denies traffic access based on the source IP address, while an extended access control list can filter packets with a higher degree of specification. It can determine the types of traffic it allows or blocks beyond just the IP address to include TCP, ICMP, and UDP, for example.
An Extended ACL can filter traffic based on the following: Source address, Destination address, Port Number, Protocol, and time range.
The extended ACL can be configured in many different ways to block potentially harmful traffic or attacks while allowing legitimate and necessary traffic through to individual destinations. Specific IP traffic in the number range of 100-199 and 2000-2699 can be prioritized. The extended access list is also generally applied close to the source.
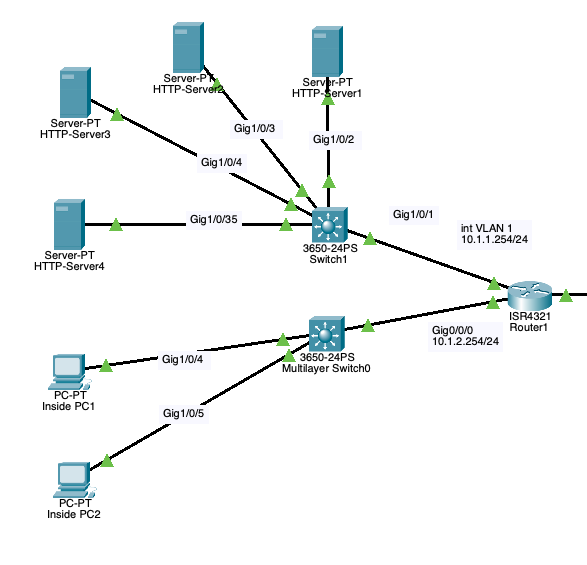
For this Lab, PC1 can only access HTTP servers 1 and 2 through HTTP and HTTPS. PC2 is not allowed to access any servers but it can access the internet. To make this possible create an ACL close to the source of the traffic that is being filtered.
This means an ACL is set at Router1 in Interface G0/0/0 inbound to allow only PC1 to access HTTP servers 1 and 2 and deny PC2 from accessing the HTTP servers. Port 80 (HTTP) and port 443(HTTPS) is set on the ACL statement to allow PC1 to access HTTP server 1 and 2 through HTTP and HTTPS. For PC2 an ACL deny statement is set to deny traffic from accessing the servers and permit any statement to allow PC2 to access the Internet
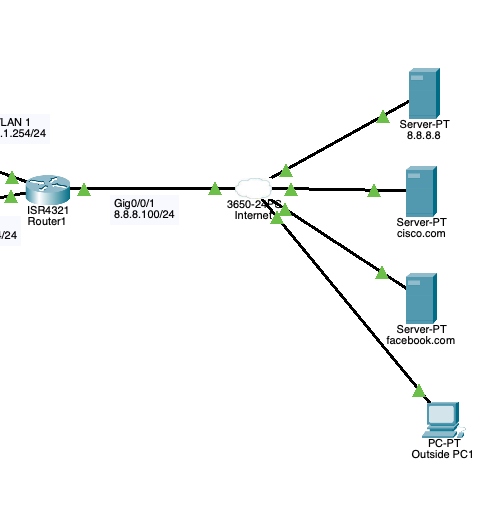
To allow external devices to access the ‘Servers’ subnet an ACL is created on the Router1 interface G0/0/1 to permit HTTP and HTTPS traffic. Another ACL is created to allow the outside Server 8.8.8.8 for the PCs to send a DNS request, to resolve the name of cisco.com or facebook.com, It allows the Host (PCs) to receive a reply from the Server 8.8.8.8 ACL statement is set again to allow Hosts (PCs) to receive traffic from any Server externally through TCP and finally another ACL statement to deny any traffic to Host (PCs) this will deny Outside PC1 to the Host (PCs) subnet but it can access the Servers Subnet.
This is a summary of my documentation.
The course can be found at Udemy by David Bombal